Current Affairs January 30, 2024: Chinese Foreign Affairs Minister visits Africa, ECOWAS, UNRWA, Accreditation System for HEIs, Bugun Community Reserve, AstroSat, RBI Guidelines on State ‘Guarantees’, Modified PKC-ERCP Link Project
Subscribers of "Current Affairs" course can Download Daily Current Affairs in PDF/DOC
Subscribe to Never Miss an Important Update! Assured Discounts on New Products!
Must Join PMF IAS Telegram Channel & PMF IAS History Telegram Channel
{GS2 – IR – Africa} Chinese Foreign Affairs Minister visits Africa
- Context (TH): The Chinese Foreign Affairs Minister visited Egypt, Tunisia, Togo and the Ivory Coast.


Objectives of visit
- China-Africa Leaders Dialogue implementation, which includes support for Africa’s industrialisation, agricultural modernisation, and cooperation on talent development.
- Crucial for the agenda of the upcoming ninth Forum on China-Africa Cooperation (FOCAC).
|
Evolution of Sino-Africa Relations
- China supported several African liberation movements during the Cold War era.
- In the 70s, African countries supported China’s permanent seat bid in the UN Security Council.
- Go Out Policy: China encouraged its companies to invest in Africa.
- In 2013, China and 52 African countries signed the Belt and Road Initiative (BRI) agreements.
- Raw Material Export: Africa’s largest trading partner & destination of one-fourth of its raw material.
- Strategic investor: The Chinese Navy stationed its first international base in Djibouti.
Chinese interests in Africa
- Natural Resources: Africa supplies 90% of the world’s cobalt and platinum and 75% of coltan, which is essential for electronics, with China having large refineries in Africa.
- African alliance and geopolitics: Africa is the largest block in UNGA and a potential supporter of contentious issues of China.
- One China Policy: Africa has supported the “One China Policy” in Taiwan and Hong Kong issues.
- Renminbi (Yuan) acceptance: With “Yuan-based panda bonds” and “debt restructuring”, China is trying to push the Yuan as an alternative to the dollar.
- African market: Africa’s young population and cheap labour force support Chinese exports.
African interests
- Financial Support: It receives investment, trade and development aid from China.
- Agriculture sector: Chinese support for hybrid crops helped Africa further its agricultural sector.
- Infrastructure: Chinese-built infrastructure and industrial parks generated employment opportunities, furthering the idea of “Made in Africa”.
- No conditionality: No conditionality on Chinese developmental aid (unlike the West) serves African authoritarian interests.
{GS2 – IR – Groupings} ECOWAS
- Context (TH): Burkina Faso, Mali, and Niger announced their immediate withdrawal from the West African bloc ECOWAS.

- Also known as CEDEAO, ECOWAS is a regional intergovernmental organization established in 1975 through the Lagos Treaty.
- Members: Benin, Cape Verde, Cote d’ Ivoire, Gambia, Ghana, Guinea, Guinea Bissau, Liberia, Nigeria, Sierra Leone, Senegal and Togo.
- Headquarters: Abuja, Nigeria.
- Objective: Creation of a “borderless region” that is well-integrated and governed by democratic principles, the rule of law, and good governance.
{GS2 – IR – UN} UN Relief and Works Agency for Palestinian Refugees ((UNRWA)
- Context (IE | LM | TOI | DH): UN agency for Palestinian refugees has suffered funding cuts from western nations after Israel accused its staff of being involved in the October 7 Hamas attack.
- Israel has also claimed that Hamas siphons off funds given to UNRWA and fights from in and around the agency’s facilities.
- Further, Israel has alleged that Hamas tunnels (are) running next to or under UNRWA facilities and accuses the agency of teaching hatred of Israel in its schools.


- UNRWA was established in 1949 by a U.N. resolution to carry out direct relief for Palestinian refugees following the Arab-Israeli War of 1948. Its mandate was later extended to include refugees from the 1967 Six-Day War.
- The Agency began operations in May 1950 and was originally expected to be short-lived.
- In the absence of a comprehensive solution to the Palestine refugee problem, the General Assembly has repeatedly renewed UNRWA’s mandate.
- UNRWA’s mandate is subject to periodic renewal every three years and has consistently been extended since its founding, most recently until June 30, 2026.
- Headquarters: Gaza City and Amman.
- UNRWA’s chief officer is the commissioner-general, who is appointed by the UN secretary-general and reports directly to the General Assembly.
- The Agency operates in the occupied West Bank, East Jerusalem, and Gaza, as well as in Jordan, Lebanon, and Syria – the neighbouring countries where the Palestinian refugees took shelter after their violent expulsion.
- It is the only UN agency dedicated to helping refugees from a specific region or conflict.
- Most of the funding for UNRWA comes from “voluntary contributions” from U.N. member states, with a small portion of its financing coming from the U.N.’s regular budget.
- The task of finding a comprehensive solution for the Israeli-Palestinian conflict and the Palestine refugee problem, however, is not part of UNRWA’s mandate but is rather the responsibility of the parties to the conflict and other political actors.
- Services provided: Education, Healthcare, Camp infrastructure and improvement, Microfinance, Emergency assistance. It also focuses on broader initiatives like infrastructure development and economic empowerment.
|
Who is a Palestine Refugees as Defined by UNRWA?Anyone whose normal place of residence was in Mandate Palestine during the period from 1 June 1946 to 15 May 1948 and who lost both home and means of livelihood as a result of the 1948 Arab-Israeli war qualifies as a Palestine refugee, as defined by UNRWA, and is eligible for UNRWA registration. |
{GS2 – Social Sector – Education} Accreditation System for HEIs
- Context (ET): NAAC introduces Binary Accreditation System for Higher Education Institutions (HEIs).
- MoE constituted an overarching committee with Dr. K. Radhakrishnan as Chairman to propose transformative reforms for strengthening the Assessment and accreditation of higher education institutions.
| National Assessment and Accreditation Council (NAAC) is an autonomous body under the UGC that assesses and certifies higher educational institutions with gradings as part of accreditation. |
Recommendations of the Committee
- Binary Accreditation (Either accredited or not accredited) rather than grades to encourage all the institutions to get on-boarded in the accreditation process.
- It will be implemented in the next four months and no new applications will be accepted as per the present methodology thereafter.
- Maturity-Based Graded Accreditation (from Level 1 to 5) to encourage accredited Institutions to raise their bar, continuously improve, and evolve in-depth or in-breadth in disciplines.
- The Maturity-based Graded levels will be implemented by December 2024.
- One Nation One Data Platform: It shall capture a superset of data from HEIs with an in-built design for collateral cross-checking to check the authenticity of data.
- Stakeholder validation has been proposed to effectively integrate stakeholders as part of the accreditation and ranking process.
- The system shall be based on Trust and Data-Driven with minimal visits to an institution for verification; however, carrying heavy penalties for giving wrong submissions.
|
{GS3 – Envi – Conservation} Bugun Community Reserve
- Context (TP I AT): Arunachal Pradesh, at the Republic Day parade, showcased its Singchung Bugun Village Community Reserve (SBVCR).
- Singchung Bugun Village Community Reserve is a 17-square-kilometre biodiversity hotspot, around 40 km from the famous Eaglenest Wildlife Sanctuary.
- The reserve was created in 2017 to protect biodiversity in the region.
- It is home to many rare and endangered species, such as the Bugun Liocichla (Liocichla bug forum) and the red panda (Ailurus fulgens), as well as various flora and fauna.
Bugun Liocichla (Liocichla bugunorum)

- It was one of the first bird species to be discovered in India since the country’s independence in 1947, and it lives only on the Buguns’ community lands.
- It was first spotted in 1995 in Arunachal Pradesh.
- However, the bird was first described in 2006 after being discovered in Eaglenest Wildlife Sanctuary by an astrophysicist, Ramana Athreya.
- It is a songbird which is named after the Buguns community.
- It is a critically endangered species, with only 14 to 20 individuals believed to exist in the world.
- It is bigger than a sparrow but smaller than a pigeon.
- A five-day Bugun Liocichla Utsav was organised in 2021 at Eaglenest Wildlife Sanctuary in AP.
Bugun Tribe
- The Buguns are an indigenous community with a population of about 2,000 people, spread across 12 villages that are dotted outside the forests of Eaglenest Wildlife Sanctuary.
- The Buguns (formerly Khowa) are one of the earliest recognised schedule tribes of India.
- Majority of them inhabit the Singchung Sub-Division of West Kameng District of Arunachal Pradesh.
- They are primarily the inhabitants of Tenga Valley, and some also dwell in the subtropical forests near Bhalukpong in the Himalayan foothills of the West Kameng district.
- It is one of India’s smallest tribal communities.
- They speak Kho-Bwa language, which is derived from the words ‘Kho’ meaning fire and ‘Bwa’ for water, hence the name Khowa.
- The chieftain makes decisions on behalf of the community and decides the functioning of the society and the use of the forest resources.
- Buguns are generally endogamous as they marry within their community. Buguns live in several exogamous clans.
- The Buguns practice shifting agriculture (jhum), which is the traditional cultivation practice of most tribes in the region.
- Like most other Himalayan tribes of Arunachal, the Buguns also originally believed in animistic beliefs and nature worship; they were initially believers of the indigenous Donyi-Polo religion until they were exposed to the Tibetan faith.
- Buguns were later on exposed to Gelugpa Buddhism (A Tibetan Faith).
- Diying Kho is the main festival of the Buguns. The Buguns also celebrate the Buddhist festivals in the same Tibetan tradition.
Community Reserves
- Conservation reserves & community reserves in India are terms denoting protected areas of India.
- These typically act as buffer zones, connectors, and migration corridors between established national parks, wildlife sanctuaries, and reserved and protected forests in India.
- Such areas are designated as conservation reserves if they are uninhabited and completely owned by the GOI but used for subsistence by communities.
- Such areas are designated as community reserves if part of the land is privately owned.
- A community reserve is usually formed by the local village council and the forest department signing a memorandum of understanding (MoU).
- After a forest has been made into a community reserve, people cannot hunt there, nor can they use it for agricultural practices, leave alone jhum.
- There were hardly any community reserves in the country before 2006. Only Karnataka, Kerala and Punjab had community reserves in 2007.
- These protected are were introduced in the Wildlife (Protection) Amendment Act of 2002.
- The provisions of the WLPA apply to an area once it has been declared a community reserve.
Eaglenest Wildlife Sanctuary (ENWS)
- ENWS is a protected area in the Himalayan foothills of West Kameng District, Arunachal Pradesh.
- It conjoins Sessa Orchid Sanctuary to the northeast and Pakhui Tiger Reserve across the Kameng River to the east.
- ENWS acquired its name from the Indian army regiment named “Eagle”, which was stationed there years ago.
- ENWS’s prime draw is that it is considered among the top birding destinations in the world.
- BirdLife International has designated Eaglenest and Sessa sanctuaries as an Important Bird Area (IBA), recognising their significance for avian conservation.
- The sanctuary plays a crucial role in protecting the habitat and migration routes of Asian elephants, especially as they move to higher altitudes in the summer.
- Organizations like the Critical Ecosystem Partnership Fund (CEPF) are actively involved in conservation initiatives.
BirdLife International
Important Bird Area
Critical Ecosystem Partnership Fund (CEPF)
|
{GS3 – IE – RBI} Guidelines on State ‘Guarantees’
- Context (TH): The RBI working group made some recommendations to address issues related to guarantees extended by State governments.
Related terms
- Creditor: Entity to whom the guarantee is given.
- Principal debtor: Defaulting entity on whose behalf the guarantee is given.
- Surety: The entity is giving the guarantee (State governments here).
Guarantees by State
- A ‘guarantee’ is a contingent liability of a State, processed by an accessory contract, that protects the lender/investor from the risk of a borrower defaulting.
- The guarantor promises to be answerable for the debt, default, or miscarriage of the latter.
Recommendation by RBI working group
Expansion of definition
- The RBI Working Group has suggested that the term ‘guarantee’ should be used in a broader sense to include all future payment obligations on the guarantor (State) to make a payment on behalf of the borrower.
- It must not make any distinction between conditional or unconditional or financial or performance guarantees to assess the fiscal risk.
According of Guarantees
- RBI working group recommended that government guarantees should not be used to obtain finance through State-owned entities, which substitute budgetary resources of the State Government.
- Additionally, they should not be allowed to create direct liability/de facto liability on the State.
- It further recommends adherence to the Government of India guidelines that stipulate that a guarantee be given only for the principal amount and normal interest component of the underlying loan.
- Furthermore, they must not be extended for external commercial borrowings.
- Guarantees must not be extended for more than 80% of the project loan and must not be provided to private sector companies/ institutions.
Risk determination
- The RBI Group suggested that States assign appropriate risk weights before extending guarantees.
- Additionally, it deemed a ceiling on issuance of guarantees as “desirable”.
- It proposes a ceiling of 5% of Revenue Receipts or 0.5% of GSDP — whichever is less.
Disclosures
- It is recommended that banks/NBFCs be directed to disclose such exposure.
- It has also sought a proper database capturing all extended guarantees.
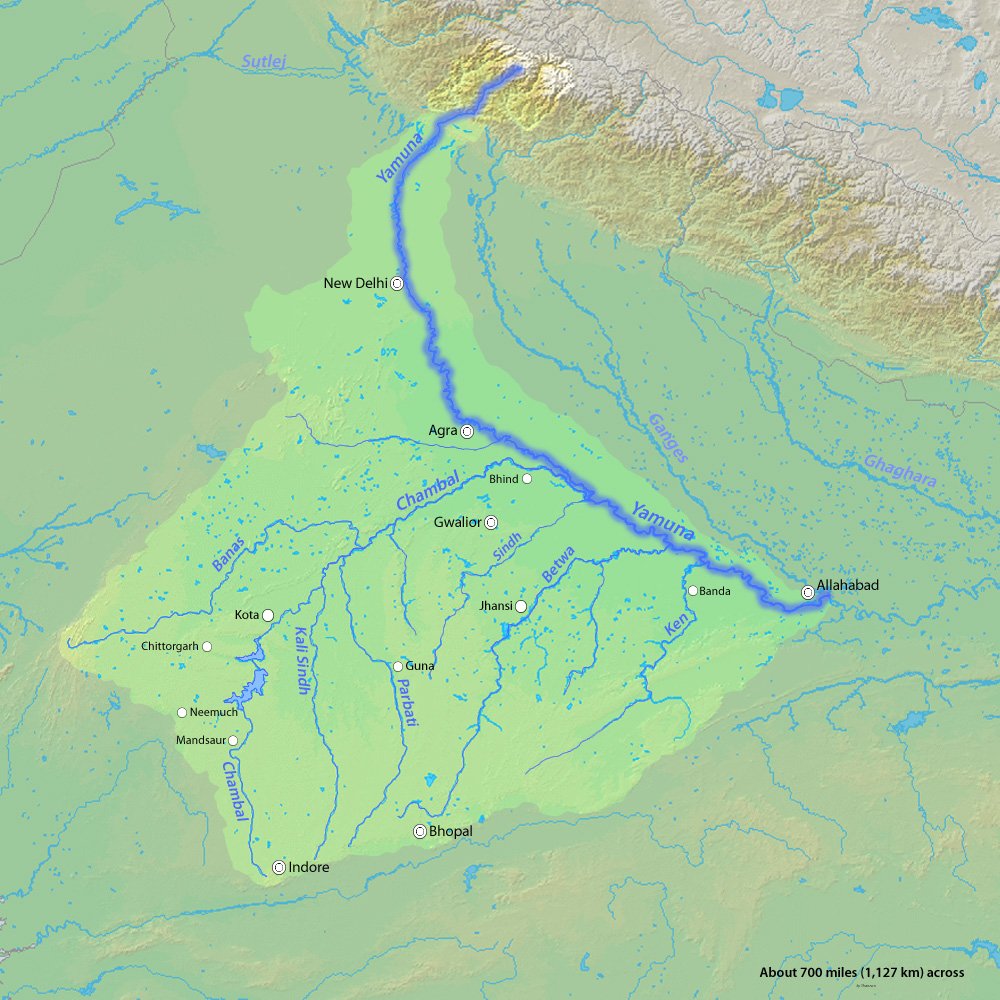
{GS3 – Infra – Initiatives} Modified PKC-ERCP Link Project
- Context (IE): Modified PKC-ERCP Project MoU was signed between Centre, Rajasthan and MP.
- Both projects are integrated under the national perspective plan of the interlinking of rivers (ILR).
Parbati-Kalisindh-Chambal (PKC) Link Project
- This project was planned to interlink Parbati-Kalisindh-Chambal (PKC).
- The 1991 report proposed the diversion of water from river Newaj (a tributary of Kalisindh) and Kalisindh to the river Chambal.
Eastern Rajasthan Canal Project (ERCP)
- It is aimed at the intra-basin transfer of water within the Chambal basin.
- It utilises surplus monsoon water available in Kalisindh, Parvati, Mej and Chakan subbasins and diverts it into water deficit sub-basins of Banas, Gambhiri, Banganga and Parbati.
- It will provide drinking & industrial water to 13 districts of eastern Rajasthan, i.e. Alwar, Bharatpur, Dholpur, Karauli, Sawai-Madhopur, Dausa, Jaipur, Ajmer, Tonk, Bundi, Kota, Baran, and Jhalawar.
- This will also benefit the Malwa and Chambal regions of Madhya Pradesh.
- Rajasthan has only 1.16% of India’s surface water and 1.72% of groundwater, with only the Chambal River basin having surplus water.
- It will cover 23.67 % of the area of Rajasthan along with 41.13 % of the population of the state.
Dependable Yield Issue
- Dependable yield means the maintainability of water supply from the source.
- Norms mandate inter-state river projects to have at least 75% dependable yield.
- However, before modification, the dependable yield was 50%.
- Modified PKC link, along with components of ERCP, have attained the divertible water available at 75 per cent dependability.
Chambal River
Kalisindh river
Parbati river
|
{GS3 – S&T – Space} AstroSat
- Context (IE): AstroSat, for the 1st time, measured X-ray polarisation from Cygnus X-1 black hole.
- AstroSat is India’s first, indigenously built, dedicated multi-wavelength space-based telescope observatory to study distant celestial objects.
- It is aimed at studying celestial sources in X-ray, optical and UV spectral bands simultaneously.
- It was launched on 28 September 2015 by ISRO into near-Earth equatorial orbit.
- The minimum useful life of the AstroSat mission is expected to be 5 years.
Objectives
- To understand high energy processes in binary star systems containing neutron stars and black holes.
- Estimate magnetic fields of neutron stars.
- Study star birth regions and high energy processes in star systems lying beyond our galaxy.
- Detect new briefly bright X-ray sources in the sky.
- Perform a limited deep-field survey of the Universe in the Ultraviolet region.

|
For details on Black Hole, visit >Black Hole
{GS3 – S&T – Tech} End to End encryption (E2E)
- Context (TH): While encryption is a robust safeguard, it is not entirely immune to vulnerabilities.
What is encryption?
- Encryption is a process of converting information or data into a code (cipher) to prevent unauthorized access by making it unreadable to those without the proper decryption key.
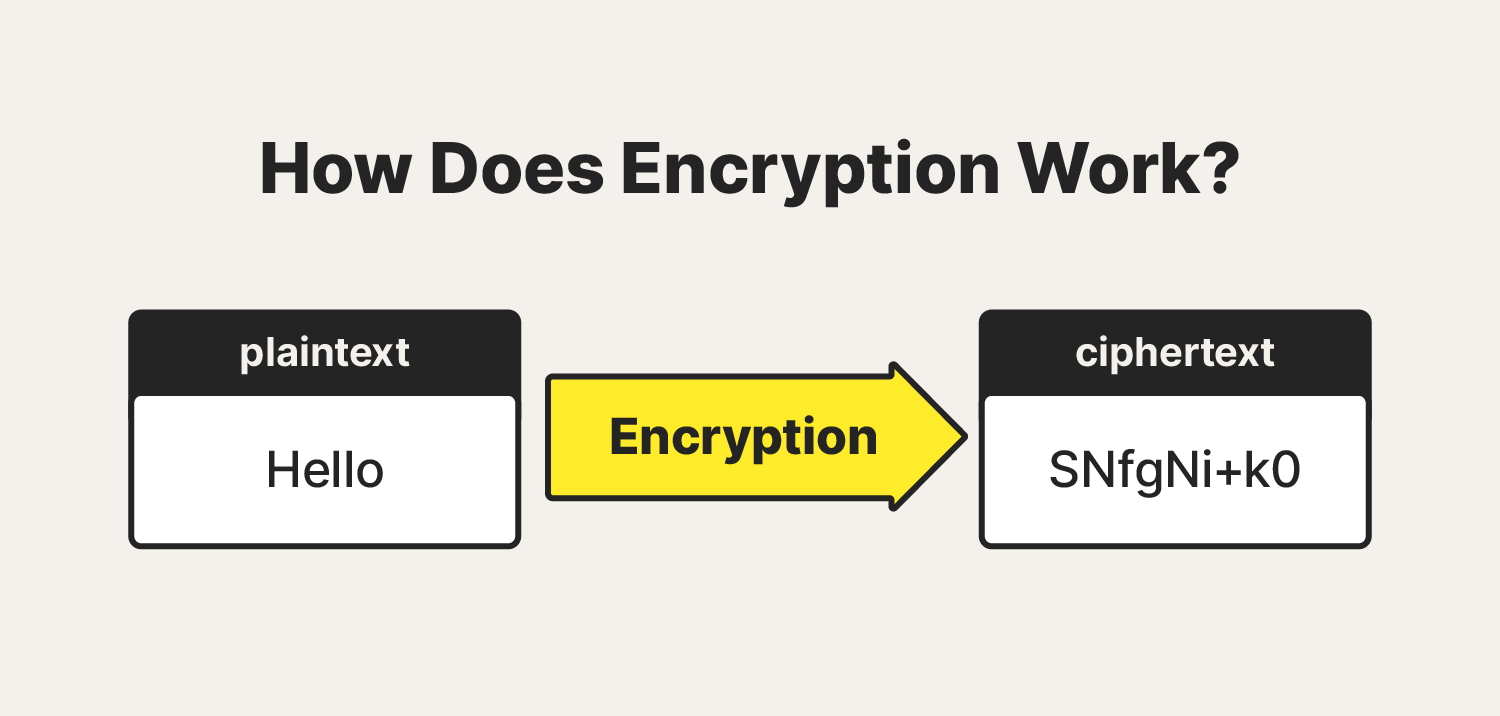
- An algorithm + key is used to encrypt/decrypt a message.
- Algorithms: are a set of instructions or rules for changing regular information into a secret code (encryption) and turning it back to regular form (decryption).
- Key: It is a string of characters used within an encryption algorithm for altering data so that it appears random.
- Public key infrastructure (PKI) governs encryption keys through the issuance and management of digital certificates.
|
- Encryption strength depends on the length of the encryption security key. However, the larger the key, the more computing time is needed to encrypt and decrypt data.
Types of encryption
|
Symmetric Encryption |
Asymmetric Encryption |
|
|
|
|
|
|
|
|
Common encryption algorithms
- Data Encryption Standard (DES): Symmetric encryption, obsolete in today’s technology ecosystem.
- Triple DES: Evolution form of DES. This method increased the key size.
- Advanced Encryption Standard: Most used encryption method today. It is much stronger than DES and triple DES.
- Twofish: The fastest symmetric encryption method and it is free to use.
- Rivest-Shamir-Adleman (RAS): Asymmetric encryption. RSA keys can be very large.
- Elliptic Curve Cryptography (ECC): Advanced form of asymmetric encryption.
|
Encryption Functions
- Confidentiality: keeps the contents of the data secret
- Integrity: verifies the origin of the message or data
- Authentication: validates that the content of the message or data has not been altered.
- Nonrepudiation: prevents the sender of the data or message from denying they were the origin.
E2E encryption vs Encryption-in-transit vs Encryption at rest
- Encryption at Rest: Here encryption is applied to the stored data. Encryption may be implemented at the source, where data is generated and stored at the origin.
- Encryption in Transit: Encrypting the data when it is transferred between two nodes of the network. The data may be stored in an unencrypted form at the source and destination storage systems.
- End-to-End Encryption(E2E): Encryption at rest + Encryption in transit. This scheme is used to prevent an actor from being able to read the contents of the message by intercepting the relay.
- Messaging apps with E2E encryption promise that even their parent companies won’t be able to read messages sent and received by its users.
Issue with E2E encryption
- A malicious actor can obtain the encryption key either of yours or your friends via MITM attack.
|
- Some potent malware can also ‘snoop’ on your messages by infiltrating your device via other means, an SMS, and reading them before they are encrypted.
- The company that installs E2E encryption on its products can install a backdoor or an exception that allows the company to surmount the encryption and access the messages.
|
- Surveillance of a user can be done by accessing the messages’ metadata (Data about the messages, such as when they were sent, to which user, how often at different times, from which location, etc.).
- Quantum computing has the potential to break existing encryption since can process a lot of data way faster than regular computers.
{Prelims – Envi – Species} Sloth Bear
- Context (DTE): Conflict between humans and sloth bears in Karnataka was in news.
- Sloth Bear are also called Honey Bear.
- They live in dry and moist forests and in some tall grasslands.
- Distribution: Sri Lanka, India, Bhutan and Nepal, predominantly in lowland areas.
- Food Habits: Eat termites and ants, fond of honey.
- Sloth bears do not hibernate.
- Tribes associated: Kalandars-Karnataka. Use bears for street performance to earn their living.
- Conservation Status: IUCN Red List: Vulnerable | CITES: Appendix I | WPA, 1972: Schedule I
- Threats: Habitat loss, poaching for body parts, captured for use in performances and hunted because of their aggressive behavior and destruction of crops.
- India has four sloth bear sanctuaries that are home to over 620 of these animals.
- The Daroji Sloth Bear Sanctuary in Karnataka, Ballari district, is Asia’s first sloth bear sanctuary.

What is Mahua?
|





![PMF IAS Environment for UPSC 2022-23 [paperback] PMF IAS [Nov 30, 2021]…](https://pmfias.b-cdn.net/wp-content/uploads/2024/04/pmfiasenvironmentforupsc2022-23paperbackpmfiasnov302021.jpg)