End to End encryption (E2E)
Subscribers of "Current Affairs" course can Download Daily Current Affairs in PDF/DOC
Subscribe to Never Miss an Important Update! Assured Discounts on New Products!
Must Join PMF IAS Telegram Channel & PMF IAS History Telegram Channel
- Context (TH): While encryption is a robust safeguard, it is not entirely immune to vulnerabilities.
What is encryption?
- Encryption is a process of converting information or data into a code (cipher) to prevent unauthorized access by making it unreadable to those without the proper decryption key.
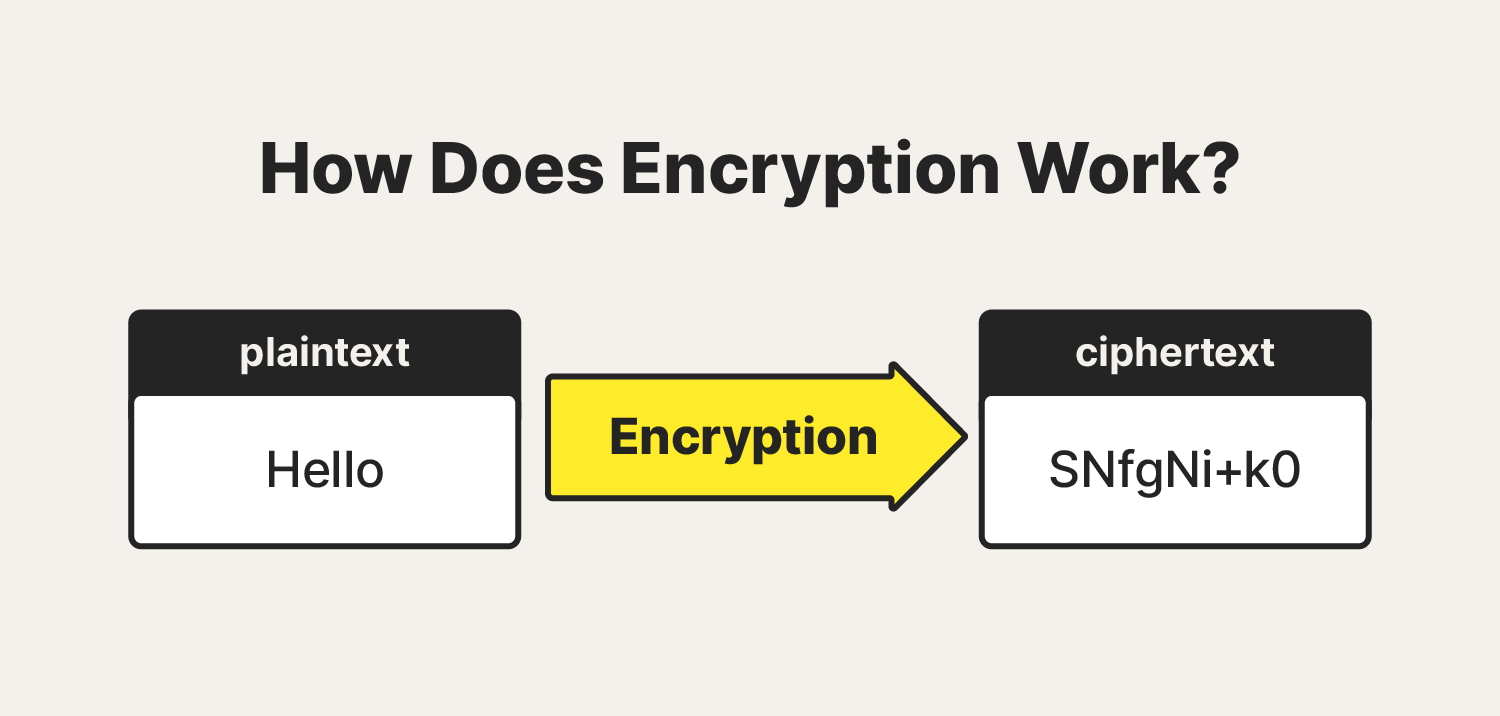
- An algorithm + key is used to encrypt/decrypt a message.
- Algorithms: are a set of instructions or rules for changing regular information into a secret code (encryption) and turning it back to regular form (decryption).
- Key: It is a string of characters used within an encryption algorithm for altering data so that it appears random.
- Public key infrastructure (PKI) governs encryption keys through the issuance and management of digital certificates.
|
- Encryption strength depends on the length of the encryption security key. However, the larger the key, the more computing time is needed to encrypt and decrypt data.
Types of encryption
|
Symmetric Encryption |
Asymmetric Encryption |
|
|
|
|
|
|
|
|
Common encryption algorithms
- Data Encryption Standard (DES): Symmetric encryption, obsolete in today’s technology ecosystem.
- Triple DES: Evolution form of DES. This method increased the key size.
- Advanced Encryption Standard: Most used encryption method today. It is much stronger than DES and triple DES.
- Twofish: The fastest symmetric encryption method and it is free to use.
- Rivest-Shamir-Adleman (RAS): Asymmetric encryption. RSA keys can be very large.
- Elliptic Curve Cryptography (ECC): Advanced form of asymmetric encryption.
|
Encryption Functions
- Confidentiality: keeps the contents of the data secret
- Integrity: verifies the origin of the message or data
- Authentication: validates that the content of the message or data has not been altered.
- Nonrepudiation: prevents the sender of the data or message from denying they were the origin.
E2E encryption vs Encryption-in-transit vs Encryption at rest
- Encryption at Rest: Here encryption is applied to the stored data. Encryption may be implemented at the source, where data is generated and stored at the origin.
- Encryption in Transit: Encrypting the data when it is transferred between two nodes of the network. The data may be stored in an unencrypted form at the source and destination storage systems.
- End-to-End Encryption(E2E): Encryption at rest + Encryption in transit. This scheme is used to prevent an actor from being able to read the contents of the message by intercepting the relay.
- Messaging apps with E2E encryption promise that even their parent companies won’t be able to read messages sent and received by its users.
Issues with E2E encryption
- A malicious actor can obtain the encryption key either of yours or your friends via MITM attack.
|
- Some potent malware can also ‘snoop’ on your messages by infiltrating your device via other means, an SMS, and reading them before they are encrypted.
- The company that installs E2E encryption on its products can install a backdoor or an exception that allows the company to surmount the encryption and access the messages.
|
- Surveillance of a user can be done by accessing the messages’ metadata (Data about the messages, such as when they were sent, to which user, how often at different times, from which location, etc.).
- Quantum computing has the potential to break existing encryption since can process a lot of data way faster than regular computers.





![PMF IAS Environment for UPSC 2022-23 [paperback] PMF IAS [Nov 30, 2021]…](https://pmfias.b-cdn.net/wp-content/uploads/2024/04/pmfiasenvironmentforupsc2022-23paperbackpmfiasnov302021.jpg)